Lua Nightmare: A Game-Breaking Exploit Threatens Garry's Mod and Its Community For over a decade, Garry's Mod has thrived as a sandbox of creativity, driven by its powerful Lua scripting capabilities and the vibrant community that builds upon it.
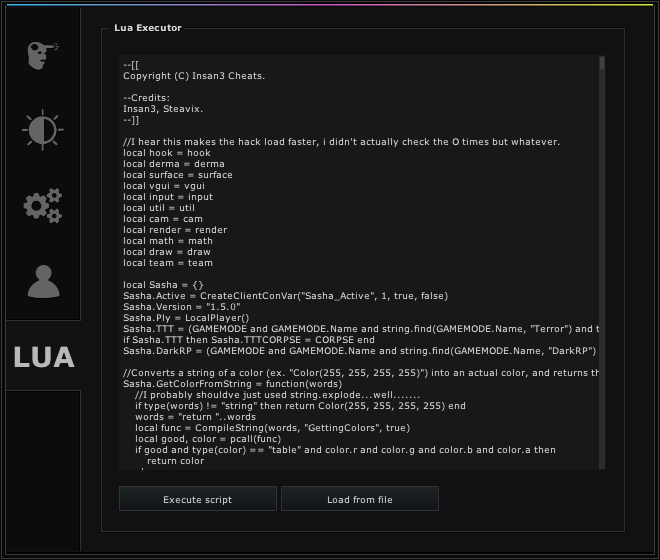
For over a decade, Garry's Mod has thrived as a sandbox of creativity, driven by its powerful Lua scripting capabilities and the vibrant community that builds upon it. But this freedom has always come with a lurking risk, and that risk has now materialized in the form of a devastating exploit dubbed "Lua Nightmare." As a seasoned addon developer and server administrator deeply embedded in the Garry's Mod ecosystem, I'm here to break down the situation, its implications, and what we can do to protect ourselves.
The Nightmare Unveiled: What is the "Lua Nightmare" Exploit?
The "Lua Nightmare" exploit allows malicious actors to remotely execute code on other players' machines via crafted addons. This means an attacker can, through seemingly harmless modifications or by repackaging existing addons with malicious code, inject arbitrary Lua code into unsuspecting users' Garry's Mod clients.
The consequences are far-reaching. Attackers could gain control of your machine, steal personal information, or even crash entire servers. The core of the problem lies in vulnerabilities within the game's networking functions, particularly net.Receive and util.AddNetworkString, combined with the infamous RunString function, which executes arbitrary Lua code.
How the Exploit Works: A Technical Overview
Imagine you download a seemingly innocent addon, perhaps something like "Enhanced Movement 2.0". Unbeknownst to you, embedded within its code is a malicious payload. This payload leverages vulnerabilities in the game's networking system to send code directly to your client and executes it, bypassing typical security measures. A common tactic involves abusing networking events to send malicious Lua code directly to the client for execution using RunString. This effectively opens the door for attackers to do anything they want on your computer.
The following code snippet demonstrates a simplified example of a vulnerable Lua function often used to exploit servers:
net.Receive("MyCustomEvent", function(len, ply)
local code = net.ReadString()
RunString(code) -- VULNERABLE!
end)
In this example, the net.Receive function is listening for a custom network event named "MyCustomEvent." When this event is triggered, the server reads a string of code from the network stream and executes it using the RunString function. If a malicious actor can send a carefully crafted string of Lua code through this event, they can execute arbitrary commands on the server.
The potential damage is immense, from keyloggers logging your Steam credentials, to turning your PC into a bot for DDOS attacks, to simply deleting all your files.
Gamemodes at Risk: Who is Most Vulnerable?
Popular gamemodes like DarkRP, Trouble in Terrorist Town, and Sandbox with custom vehicle systems (like Simfphys) are particularly vulnerable. These gamemodes often rely heavily on custom addons and extensive networking. The more addons and networking involved, the larger the attack surface becomes. A single compromised addon can serve as a gateway to widespread infection across a server and its players.
A Decade of Development, a Lingering Concern
As someone who has developed Garry's Mod addons for over a decade, I've always known about the potential for these kinds of exploits. The beauty of Lua scripting is its flexibility, but that flexibility is also its greatest weakness.
The lack of robust security measures within Garry's Mod, and the reactive approach to DMCA enforcement has created a breeding ground for malicious actors. While I appreciate the freedom that Garry's Mod offers, it is frustrating that more preventative security measures haven't been implemented. It's time for a fundamental shift towards proactive security to protect the community.
Mitigation Strategies: Protecting Your Server and Yourself
While we wait for Valve to address the core vulnerabilities, server administrators and players alike need to take immediate action.
For Server Administrators:
- Disable Vulnerable Lua Functions: This is a drastic measure, but consider disabling the
RunStringfunction entirely or restricting its use to trusted addons. A server administrator can do this through the server.cfg file with the command:lua_run_cl gamemode.Call("DisableFunction", "RunString"). Be aware that this may break some addons and is not a perfect solution, but it provides a basic first step. - Implement Whitelist Systems: Carefully curate a list of trusted addons and only allow those to be installed on your server. Utilize Steam Workshop collections and enforce those collections during server startup. Regularly review your whitelist and remove any addons that are no longer maintained or have a questionable reputation.
- Monitor Server Logs: Keep a vigilant eye on your server logs for suspicious activity. Unusual function calls, unexpected network traffic, and errors related to Lua scripting are all potential red flags. Consider using tools like GLuaMonitor to assist with this process.
- Sanitize Input Data: This is critical. Never trust data received through networking functions without thorough sanitization. Use
util.JSONEncodeandutil.JSONDecodeto ensure data is properly encoded and sanitized before use in networked functions. This can help prevent code injection attacks. - Regularly Update Addons: Ensure all your addons are up-to-date. Developers often release updates to address security vulnerabilities. Staying current is a crucial step in protecting your server.
- Educate Your Players: Inform your players about the risks of downloading untrusted addons. Encourage them to report any suspicious activity they encounter. A well-informed community is your best defense.
For Players:
- Be Wary of Addons: Only download addons from trusted sources. Check the addon's ratings, reviews, and creator's reputation before subscribing.
- Question Permissions: Be suspicious of addons that request unnecessary permissions or access to sensitive data.
- Report Suspicious Activity: If you notice anything unusual, such as performance issues, crashes, or unexpected behavior, report the addon to the Steam Workshop and inform the server administrator.
- Keep Your System Updated: Ensure your operating system and antivirus software are up-to-date. This can help protect your system from malware that might be installed through the exploit.
The Imperative for Action: A Call to Valve and the Community
I implore Valve to take the "Lua Nightmare" exploit seriously and address it immediately. This requires implementing more robust security measures, improving the addon verification process on the Steam Workshop, and providing server administrators with better tools to defend their servers. Stricter code analysis on addon submissions, sandboxing Lua execution, and implementing better network security protocols are all crucial steps.
I also call on the Garry's Mod community to unite and be vigilant. Report suspicious addons, educate yourselves on Lua security best practices, and support developers who prioritize security in their addons. We must work together to create a safer and more secure environment for everyone.

Conclusion: Securing the Future of Garry's Mod
The "Lua Nightmare" exploit is a stark reminder of the importance of security in the Garry's Mod ecosystem. The freedom and creativity that define Garry's Mod must be balanced with robust security measures to protect players and servers from malicious attacks. By taking proactive steps to mitigate the risks, reporting suspicious activity, and demanding better security from Valve, we can work together to secure the future of Garry's Mod and ensure that it remains a safe and enjoyable platform for everyone. The time to act is now, before the "Lua Nightmare" becomes a full-blown reality.